We are excited to announce that Docker Scout General Availability (GA) now allows developers to continuously evaluate container images against a set of out-of-the-box policies, aligned with software supply chain best practices. These new capabilities also include a full suite of integrations enabling you to attain visibility from development into production. These updates strengthen Docker Scout’s position as integral to the software supply chain.
For developers building modern cloud-native applications, Docker Scout provides actionable insights in real-time to make it simple to secure and manage their software supply chain end-to-end. Docker Scout meets developers in the Docker tools they use daily, and provides the richest library of open source trusted content, policy evaluation, and automated remediation in real-time across the entire software supply chain. From the first base image pulled all the way to git commit, CI pipeline, and deployed workloads in production, Docker Scout leverages its large open ecosystem and the container runtime as vehicles for insights developers can easily act upon.
With Docker Scout operating as the system of record for the software supply chain, developers have access to real-time insights, identification of anomalies in their applications, and automated recommendations to improve application integrity, in tandem with Docker Desktop, Docker CLI, Docker Hub, and the full suite of Docker products. Docker Scout is designed to see the bigger picture and address challenges that are layered into the software supply chain.
Software supply chain
Through many in-depth conversations with our customers, we uncovered a clear trend: Developers are increasingly aware about not consuming content they don’t trust or haven’t permitted within their accepted range of organizational policies. To solve for this, Docker provides Docker Official Images, a curated set of Docker repositories hosted on Docker Hub. These images provide essential base repositories that serve as the starting point for most users. Docker and Docker Scout will continue to provide additional forms of software supply chain metadata for the Docker Official Image catalog in the coming months.
Trusted content is the foundation of secure software applications. A key aspect of this foundation is Docker Hub, the largest and most-used source of secure software artifacts, which includes Docker Official Images, Docker Verified Publishers, and Docker-Sponsored Open Source trusted content. Docker Scout policies leverage this metadata to track the life cycle of images, generate unique insights for developers, and help customers automate the enhancement of their software supply chain objectives — from inner loop to production.
Ensuring the reliability of applications requires constant vigilance and in-depth software design considerations, from selecting dependencies with a JSON file, running compilations and associated tests, to ensuring the safety of every image built. While some monitoring platforms focus solely on policies for container images currently running in production, the new Docker Scout GA release recognizes this is not sufficient to oversee the entire software supply chain, since that approach occurs too late in the development process.
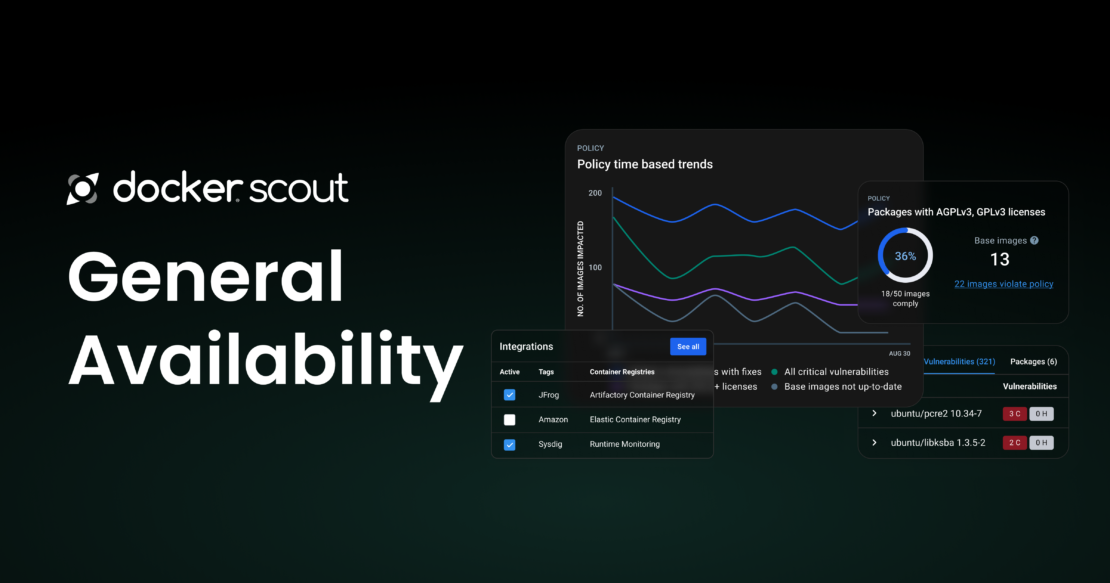
Docker Scout offers a seamless set of actionable insights and suggested workflows that meet developers where they build and monitor today. These insights and workflows are particularly helpful for developers building Docker container images based on Docker Trusted Content (Docker Official Images, Docker-Sponsored Open Source, Docker Verified Publishers), and for many data sources beyond that, including data sourced from integrations with JFrog Artifactory, Amazon ECR, Sysdig Runtime Monitoring, GitHub Actions, GitLab, and CircleCI (Figure 1).
Figure 1: Integrate Docker Scout with tools you already use.
Policy evaluation
Current policy solutions support only a binary outcome, where artifacts are either allowed or denied based on the oversimplified results from policy analysis. This pass/fail approach and the corresponding gatekeeping is often too rigid and does not consider nuanced situations or intermediate states, leading to day-to-day friction around implementing traditional policy enforcement. Docker Scout now goes deeper, not only by indicating more subtle deviations from policy, but also by actively suggesting upgrade and remediation paths to bring you back within policy guidelines, reducing MTTR in the process.
Additionally, Docker Scout Policy makes for a productivity boost that stems from not having to wait for CI/CD to finish to know if you need to upgrade dependencies. Evaluating policies with Docker Scout prevents last-minute security blockers in the CI/CD that can impact release dates, which is one of the primary reasons teams tend not to adopt policy evaluation solutions.
Policy can take many forms: Specifying which repos or sources it is safe to pull in components or libraries from, requiring secure and verified build processes, and continuously monitoring for issues after deployment. Docker Scout is now equipped to expand the types of policies that can be implemented within these wider sets of definitions (Figures 2 & 3).
Figure 2: Docker Scout dashboard showing policy violations with fixes.
Figure 3: Overview of the security status of images across all Docker-enabled repos over time.
Policy for maximal coverage
Our vision for policy is to allow developers to define what’s most developer-friendly and secure for their needs and their environments. While there’s a common thread across some industries, every enterprise has nuances. Whether setting security policies or aligning to software development life cycle tooling best practices, Docker Scout’s goal is to continuously evaluate container images, assisting teams to incrementally improve security posture within their cloud infrastructure.
These new capabilities include built-in out-of-the-box policies to maintain up-to-date base images, track associated vulnerabilities, and monitor for relevant in-scope licenses. Through evaluation results, users can see the status of policies for each image. Users will have an aggregated view of their policy results so they know what to focus on, as well as the ability to evaluate those results in more detail to understand what has changed within a given set of policies in a repo list view (Figure 4).
Figure 4: View from the CLI.
What’s next?
Docker Scout is designed to be with you in every step of improving developer workflows — from helping developers understand which actions to take to improve code reliability and bring it back in line with policy, to ensuring optimal code performance.
With the next phase on the horizon, we’re gearing up to deliver more value to our customers and always welcome feedback through our Docker Scout Design Partner Program. For now, the Docker Scout team is excited to get the latest solutions into our customers’ hands, ensuring safety, efficiency, and quality in a rapidly evolving ecosystem within the software supply chain.
Developers in our Docker-Sponsored Open Source (DSOS) Program will soon be able to access our Docker Scout Team plan, which includes unlimited local image analysis, as well as up to 100 repos for remote images, SDLC integrations, security posture reporting, and policy evaluation. Once Docker Scout is enabled for the DSOS program in late 2023, DSOS members can enable it on up to 100 repositories within their DSOS-approved namespace.
To learn more about Docker Scout, visit the Docker Scout product page
Learn more
Try Docker Scout.
Looking to get up and running? Use our Quickstart guide.
Vote on what’s next! Check out the Docker Scout public roadmap.
Have questions? The Docker community is here to help.
New to Docker? Get started.
Quelle: https://blog.docker.com/feed/
Published by