Here Are The 294 Accounts Donald Trump Retweeted During The Election
With the touch of the retweet button, Donald Trump — who has some 17.5 million followers — can program the news cycle. He can amplify formerly unknown accounts, signal what voices he's listening to, and tacitly endorse individuals and ideas, no matter how controversial: Trump, more than any politician or powerful figure with access to a smartphone, understands and uses the now-cliche “retweets are not endorsements” maxim to his advantage.
To better understand which individuals and institutions the President-elect relies on as social media surrogates, BuzzFeed News compiled a complete list of users Trump has retweeted since he launched his presidential campaign.
We reviewed 26,377 of Trump’s 34,152 tweets, which we received through the Twitter API and developer Brendan Brown, who has archived Trump’s tweets beyond what is accessible via the API (a stream of data that includes information like tweet text, time, and date). We filtered that data down to the 2,760 hyperlinks tweeted by Trump’s personal Twitter account since he announced his candidacy in June 2015 up until December 15 of this year.
By programmatically expanding the links we were able to narrow them down to the links he tweeted from Twitter (retweets show up as links from twitter.com when downloaded as data), filtered out the ones that were media tweets and were left with all the manual, regular and quote tweets Trump had sent through his account. Fourteen of the accounts that Trump has retweeted are no longer active. Among those fourteen, five accounts — White GenocideTM, babo_siren, Campaign_Trump, patrioticpepe, and TMoody — were suspended (Twitter suspends accounts when users violate its rules, most commonly if the account spams people, may have been hacked, or is engaging in abusive behavior).
Analysis of the accounts Trump has retweeted reveals several distinct patterns:
Trump appears willing to retweet almost anyone. Unlike most mainstream politicians, who carefully select the accounts they&039;ll amplify, Trump is comfortable retweeting a truly diverse array of accounts. Just last month, the President-elect retweeted a 16 year-old from California as evidence to support a Twitter feud with CNN. He does not discriminate based on number of followers (he retweeted an account with just 2 followers), number of tweets (he retweeted the first tweet from a woman who, to date, has only tweeted five times), or the contents of someone&039;s account bio (he retweeted one user whose bio at the time was: “Mexico, get ready to receive your finest citizens back! Rapists, Thieves & Perverts”).
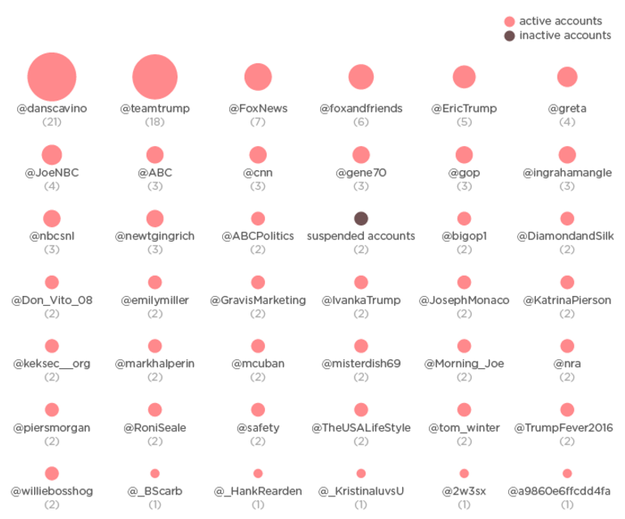
But he is most likely to boost the signal from his inner circle and friendly members of the press. The accounts he retweets the most were those of campaign advisors and some chosen members of the press, including his social media lead, Dan Scavino (21 RTs); his son, Eric Trump (5); Fox News&039; Greta Van Susteren (4); MSNBC host Joe Scarborough (4); former House Speaker Newt Gingrich (3); Lifezette editor and conservative pundit Laura Ingraham (3); and Bloomberg Politics&039; Mark Halperin (2).
The President-elect, despite his repeated claims of a deeply biased mainstream media, retweets a high number of legacy media outlets. Among his most tweeted news accounts: Fox News (7 RTs), Fox And Friends (6), ABC (3), CNN (3), and Morning Joe (2). In nearly every instance, the retweeted accounts shared news items or memes about polls that favored Trump (many from the primaries), or negative articles about Hillary Clinton — many of them aggregations of WikiLeaks emails. Trump also appears to be eager to promote positive news about him from pop culture and entertainment accounts, as evidenced by his retweeting Saturday Night Live&039;s account three times.
On occasion, Trump will retweet a user from the other side of the aisle. This tends to happen under two circumstances:
#1) When an account says something positive about him (in one instance, Trump retweeted former Obama Senior Advisor Dan Pfeiffer, who suggested Trump understood the internet better than most democrats):
2.) To attempt to attack his opponents — as he did here last June with Hillary Clinton:
He has retweeted accounts with clear ties to the alt-right on numerous occasions. Trump recently told the New York Times he disavowed the movement and suggested he didn&039;t “want to energize the group.” However, throughout the 2016 campaign, Trump retweeted three separate users with the words “alt-right” in their bios. He retweeted “WhiteGenocideTM,” and four with “#nationalist” in their bios. One account that the President-elect retweeted (a bot, it turns out) had the phrase “#GoebbelsMindset” in the bio — a reference to Joseph Goebbels, the Nazi propaganda minister in Hitler&039;s Germany
Other items of note include:
- 151 of the 294 individual accounts Trump retweeted during the campaign mention the word “Trump” in the bio or account display name.
- 22 accounts have the Make America Great Again hashtag, #MAGA, in theirs.
-14 accounts have the word “deplorable” in the bio or account display name.
- 9 accounts have the word “veteran” in the bio or account display name.
- 2 accounts have a frog emoji in the bio or account display name, presumably a reference to Pepe.
But there&039;s no better way to get a peek into Trump&039;s Twitter mindset than to explore the accounts he&039;s retweeted for yourself. Below, we&039;ve included every account he&039;s retweeted, in order of the number of times Trump has RT&039;d the account (Of note: the bios and follower counts are current as of when BuzzFeed News scraped the data on December 7th, 2016, and may not necessarily reflect the bio or follower accounts on the day Trump retweeted them). There&039;s also a full graphic at the end of the list.
KEY:
ACCOUNT DISPLAY NAME (FOLLOWERS): ACCOUNT BIO.
21 Retweets:
Dan Scavino Jr (241,484 followers): June 2015 – Current: Director of Social Media & Senior Advisor to President-elect Donald J. Trump #Transition2017 • #TrumpTrain Conductor
18 Retweets:
Official Team Trump (372,885 followers): Welcome To The Official #TeamTrump Account. Together, We WILL #MakeAmericaGreatAgain&033; #AmericaFirst
7 Retweets:
Fox News (12,068,826 followers): America’s Strongest Primetime Lineup Anywhere&033; Follow America&039;s 1 cable news network, delivering you breaking news, insightful analysis, and must-see videos.
6 Retweets:
FOX & Friends (700,152 followers): America&039;s 1 cable morning news show
5 Retweets:
Eric Trump (725,051 followers): EVP of Development & Acquisitions, The Trump Organization. Founder of EricTrumpFDN benefiting StJude Children&039;s Research Hospital. Husband to LaraLeaTrump
4 Retweets:
Joe Scarborough (653,550 followers): We can love completely without complete understanding.
Greta Van Susteren (1,109,570 followers): Retweets are just retweets; RT does not mean I agree or disagree….I am merely retweeting;check out video reports https://t.co/BpGqSgCJU9
3 Retweets:
GENE (7,535 followers): blocked by rosie followed by marcuslemonis boygeorge & scottBaio Legal Italian Immigrant. Proud US Citizen,World Traveler With 25 Years of Business Dealings
Newt Gingrich (1,784,072 followers): Husband, father, grandfather, citizen, small businessman, author, former Speaker of the House.
Laura Ingraham (1,118,943): Mom, Editor-in-Chief of LifeZette. Host, The Laura Ingraham Show, 9 to Noon ET. Listen live, join Laura365 to listen 24/7. Fox News. https://t.co/Wu93dy29HT
ABC News (8,248,722 followers): See the whole picture with ABC News. Join us on Facebook: https://t.co/ewMNZ54axm
Saturday Night Live (1,749,560): The official Twitter handle for Saturday Night Live. Saturdays at 11:30/10:30c&033; #SNL
GOP (1,056,143 followers): Updates from the Republican National Committee #LeadRight2016
CNN (30,043,735 followers): It’s our job to #GoThere and tell the most difficult stories. Come with us&033;
2 Retweets:
Trump 4 Women (14,198 followers): SEE TheTRUMPetts 1 OFFICIAL TRUMP TRAIN Vid TeamTRUMP HIT SONGWRITERS =USMC / LEO VETS
Don Vito (23,804 followers): American Patriot MakeAmericaGreatAgain AmericaFirst
TheAmericanLifeStyle (3,616 followers): Our American journey Start Now. •blest• TeamTrump #TrumpPence16 MAGA DonaldJTrumpJr IvankaTrump EricTrump TiffanyATrump
Deplorable Vlad (8,582 followers): Waterboarding&039;s too good for them. I&039;m staking my vote on TRUMP&033;
Diamond and Silk® (197,218 followers): #STUMP4TRUMPBABY #CHOOCHOOBABY #DITCHANDSWITCHNOW #STUMP4TRUMPGIRLS #TheUnitedStatesNotTheDividedStates
Trump Phenomenon (2,863 followers): Trump Landslide 2016
Willie Robertson (2,441,160 followers): President of Duck and Buck Commander. Personality on both, Duck Dynasty and Buck Commander Protected by Under Armour.
Morning Joe (280,073 followers): Live tweet during the show&033; Links to must-read op-eds and other features. Feed managed by MJ staff. Retweets not necessarily endorsements.
Gravis Marketing (2,823 followers): Gravis Marketing is a communications company, specializing in public opinion polls, public relations, political strategy, and research.
Roni Seale (6,210 followers): But Jesus beheld them, and said unto them, With men this is impossible; but with God all things are possible.
Matthew 19:26 (KJV)
Piers Morgan (5,292,866 followers): &039;&039;One day you&039;re the cock of the walk, the next a feather duster.&039;
Mark Halperin (253,218 followers): Managing editor, Bloomberg Politics; host, With All Due Respect; correspondent/EP, SHO_TheCircus; co-author, Game Change & Double Down
Safety (3,215,464 followers): Helping you stay safe on Twitter.
#NRA (4,13,722 followers): National Rifle Association of America NRA
Emily Miller (58,635 followers): Senior Political Correspondent OANN. Armed. Wannabe Surfer. Author of Emily Gets Her Gun. https://t.co/kuOGeQfYgc
Ivanka Trump (2,498,905 followers): Wife, mother, entrepreneur. EVP, Trump Org. Founder, https://t.co/qWTVy424t8. Author, Women Who Work: Rewriting the Rules for Success (out in March)
Joseph Monaco (2,567 followers): I HATE racists&033; Proud to be followed by Bill Mitchell Mitchellvii I&039;m strongly supporting Mr. Trump for President&033; TrumpPence16 #NYPD #FDNY TrumpTrain MAGA
Tom Winter (12,664 followers): NBC News Investigations reporter based in NYC focusing on Police, Courts, Corruption, Financial Fraud, and Homeland Security stories across the Eastern U.S.
Jason Bergkamp (59,251 followers): #keksec | #NS | Nationalist ✠ | 0.2% Chosen and proud | An Anglo&039;s worst adversary | GoebbelsMindset
Katrina Pierson (242,737 followers): Senior Advisor Transition2017 & Former realDonaldTrump Natl Campaign Spokeswoman MakeAmericaGreatAgain Transition2017 MAGA
ABC News Politics (306,398 followers): Following ABC News&039; political team with tweets by: aabramson evanmcmurry and nickirossoll
Mark Cuban (6,040,253 followers): #DallasStrong
1 Retweet:
Richard Hernandez (979 followers): Formerly NVGOP. Conservative. Originalist. Prior intern at Kramerica Industries. Tweets are my own. Temeculan.
Trump2016Media (3,528 followers): My #Trump2016 Website is Updated Daily: 1000+ Interviews & Rallys, Articles, News, Media realDonaldTrump TrumpTrain MakeAmericaGreatAgain
Electra Goldwell (284 followers): I want God to make America Great again&033;
Amy Colley Tyson (403 followers): Follower of Christ, Wife, Mother, Family Nurse Practitioner, Former Miss Tennessee USA 2005, Supporter of H. Res. 752 and Animal Hope and Wellness Foundation
Donald Trump Florida (5,231 followers): Donald J. Trump for President (Florida – Official)
MariaRandisiErnandez (989 followers): Special Education Teacher &(Child Advocate).Interests:ELVIS, Hollywood,Music, Politics,Travel, Working Out,#TrumpStrong MAGATrumpTrain
*NO LISTS or B Blocked
RealBill (47 followers): [No Bio Listed]
Politics Today (54,257 followers): || CONSERVATIVE NEWS NETWORK|| News/Politics/Opinion – Reporter/Pundit #PoliticsToday Articles/Commentary Facebook: https://t.co/7wFggE8CL2 #Fact
Montana4Trump (1,452 followers): God Bless America. Conservative Catholic mother-daughter team Tweeted by: realDonaldTrump, mercedesschlapp, MattSchlapp, ktmcfarland.
USA For Trump 2016 (80,568 followers): Official USA for Trump 2016 Follow our new President Trump News Page TrumpsNewsDaily for great Trump news articles about his presidency&033;
Political Polls (46,266 followers): We are a non-partisan group dedicated to keep you informed with recent political polls from trusted polling companies and predictions from reputable pundits.
Antonio Valencia (18 followers): [No Bio Listed]
Karen Posey (15 followers): [No Bio Listed]
JohnnyBoy (2 followers): [No Bio Listed]
Corey R. Lewandowski (175,221 followers): CNN Political Commentator and former Campaign Manager for Donald J. Trump for President. MakeAmericaGreatAgain Trump2016
Eustace Bagge (291 followers): As seen on Fortune, Time, CSPAN. Aspiring Frogtwitterati.
Citizen Dale (19024 followers): Ind Engineer & business owner. Captain-Trumptbird Calling Team We&039;ve made over 80,000 calls for Donald J Trump&033; Producer of the Monster Vote video for Trump&033;
Deplorable C Lewis (1,223 followers): I VOTED for DONALD TRUMP FOR PRESIDENT If you support DONALD SPREAD THE TRUMP MESSAGE. #Trump45 #POTUS45 #DrainTheSwamp
Deplorable MP95B (15,705 followers): US Army MP Veteran (No Combat) firm believer in US Constitution & 2A. NRA Lifetime Member. Strong Trump supporter. MakeAmericaGreatAgain Trump2016 NRA #FL
RSBN TV (38,820 followers): Right Side Broadcasting Network. Following realdonaldtrump wherever he goes. 1 source for live political event coverage.
DiCristo Trump Won (4,833 followers): Love For God & Country. Make America Great Again&033; American Revolution Part Deus&033; TRUMP&033; Nov8 win gave us fighting chance&033; we have to beat Elites&033; MAGA
Polling Hub (44 followers): Polling averages for the 2016 U.S. presidential primaries. Accurate and up to date, we&039;re the most detailed poll aggregator tracking the 2016 presidential race.
Deplorable-Sweetie (22,432 followers): #Trumpette Put Americans first&033; Trump2016 ˚(*❛‿&x275B;)/&x2DA; MAKE AMERICA GREAT AGAIN&033; I will fight for MY PEOPLE. Nationalist No rapefugees or illegals&033; TrumpStrong
Italians For Trump (57,540 followers): We are ITALIAN-AMERICANS who proudly support realDonaldTrump our President-elect of the USA&033; #Italians4Trump DrainTheSwamp MAGA #PEOTUS #IoVotoNo
NEPA for TRUMP (26,889 followers): Official realDonaldTrump Northeastern Pennsylvania #TeamTrumpPA Trump2016 MakeAmericaGreatAgain TeamTrump AmericaFirst #ImWithYou TrumpTrain TrumpPence16
TrumpCoastOfSC (8,678 followers): Retweets & quoted tweets do not equal endorsement or agreement. Follow me also at https://t.co/bkXkkAj4cU
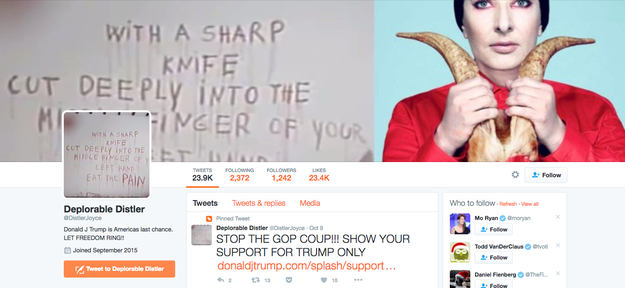
Deplorable Distler (1,247 followers): Donald J Trump is Americas last chance. LET FREEDOM RING&033;&033;
Bryan Ranzetta (260 followers): when kids look at me I say this is because I didn&039;t eat my vegetables
Elsa Aldeguer (1752 followers): Proud Latina Trump supporter from Los Angeles California God bless America and our New President Donald J Trump
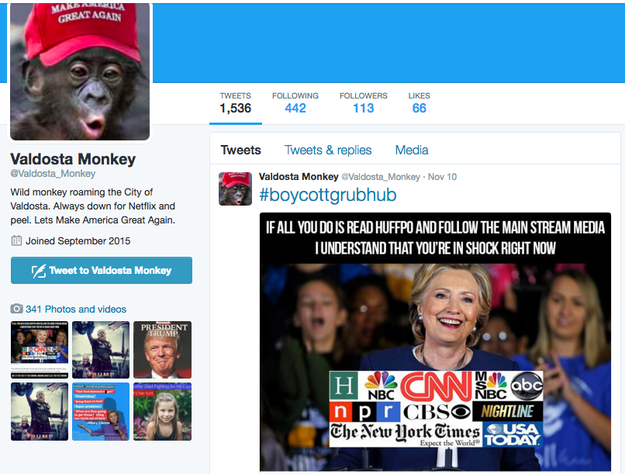
Valdosta Monkey (116 followers): Wild monkey roaming the City of Valdosta. Always down for Netflix and peel. Lets Make America Great Again.
Quelle: <a href="Here Are The 294 Accounts Donald Trump Retweeted During The Election“>BuzzFeed






