
Nandan Nilekani
Manjunath Kiran / AFP / Getty Images
Three years after Nandan Nilekani, the high-profile tech entrepreneur who helped create India’s controversial biometric identity program called Aadhaar, publicly tweeted his own confidential Aadhaar ID, his personal information is still readily available online, BuzzFeed News has learned.
An Aadhaar ID, which is associated with personal information like your address and birthdate, and is linked to services such as your bank account, tax records, cellphone number, and insurance, is like an extreme form of a social security number in the US, which is also connected to your biometric data.
From 2009 to 2014, Nilekani served as the head of the Unique Identification Authority of India (UIDAI), the government agency responsible for administering Aadhaar. The program aims to create a digital national identity system by collecting the personal details and biometrics — all 10 fingerprints and iris scans — of 1.3 billion Indian residents into a government-owned database. Critics have slammed Aadhaar, saying it violates privacy, enables state surveillance, and exposes citizens to identity theft.
Nilekani exposed himself to identity theft by tweeting a picture of his own Aadhaar card on April 12, 2014. He blacked out the first eight digits of his 12-digit Aadhaar number, but did not obscure the QR code containing his personal demographic details that could be read by any freely available iOS or Android app used for scanning QR codes.
And as with just about anything that’s publicly tweeted, Nilekani’s private information remains online. Members of an internet forum popular with computer programmers scanned his QR code and posted his demographic details and Aadhaar number, and this data eventually ended up on at least half a dozen other web pages that BuzzFeed News reviewed. Images of Nilekani’s tweet with his Aadhaar card exist on at least one popular website.
Despite several people on Twitter pointing out a potential breach of privacy, Nilekani’s tweet remained on Twitter at least through September 2016, when he finally deleted it.
“I guess Nandan didn’t realize what he had done at first,” said Prasanto K Roy, a former technology journalist who was one of the people who alerted Nilekani. “And I don’t think he paid much attention to it even when it was flagged, probably thinking that it wasn’t a big deal since, as a well-known person and the head of the Aadhaar program, most of his demographic details were publicly available anyway. I think he must have realized the seriousness of it later — that his tweet might suggest to others that it was OK to post a picture of your Aadhaar card simply by redacting the Aadhaar number itself.”
In September 2016, India’s government passed the Aadhaar Act to govern the program, which made publishing an Aadhaar number publicly a criminal offence.
Nilekani did not respond to BuzzFeed News’ requests for comment. But a source close to him said under the condition of anonymity that they advised him to take down his tweet for almost six months — starting a few months before the Aadhaar Act was introduced — before it was finally deleted.
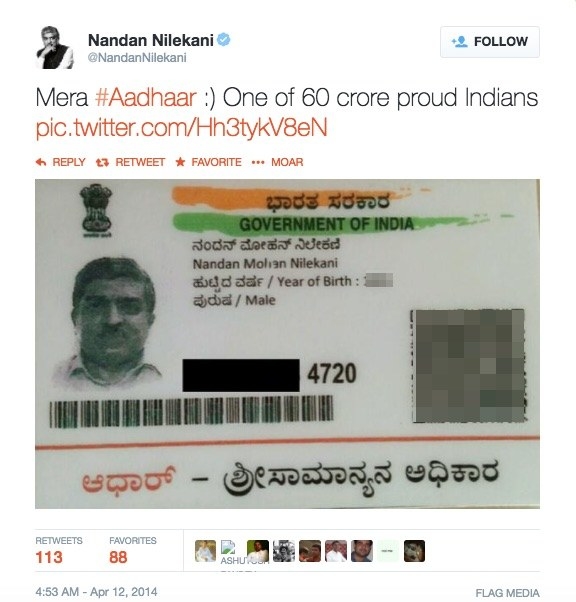
A screenshot of Nilekani's tweet. (BuzzFeed News redacted the identifying QR code.)
Experts said that Nilekani’s leaked Aadhaar number leaves him vulnerable to identity fraud because the Indian government requires citizens to link their Aadhaar numbers to essential services like food subsidies, utilities, bank accounts, cellphone numbers, and insurance services.
“Personal data such as full names, birthdates, and residential addresses should always be afforded a high level of protection,” cybersecurity expert Troy Hunt told BuzzFeed News. “For many people, this is information they won’t want to share beyond authorized parties because it can be used to locate them or aid in identity theft.”
BuzzFeed News, for instance, was able to find out where Nilekani does his banking by using a publicly available, UIDAI-provided service that lets anyone simply punch in an Aadhaar number on a mobile phone to see the bank accounts it is linked to.
Indeed, despite the UIDAI’s repeated denials, Aadhaar numbers leaked online have been used to commit identity theft in India. In October 2017, for instance, Indian police arrested a group that used the leaked Aadhaar numbers of nearly 300 pensioners to open bank accounts in their names and swindled over four million Indian rupees worth of pension money over two years, according to reports.
Making things murkier is the UIDAI’s conflicting messaging about whether an Aadhar ID is actually private information or not. After The Tribune published an investigation revealing how it was able to buy unauthorized access to the demographic details of nearly 1.2 billion Indians in the Aadhaar database earlier this week, the UIDAI said having someone’s Aadhaar number and demographic information was “not a security threat” without also having their biometric information. But a day later, the agency sent out a tweet cautioning the general public about the importance of keeping Aadhaar numbers confidential.
“Their claim about demographic information being useless without biometrics is simply not true,” said Pranesh Prakash, policy director at the Centre for Internet and Society, a Bangalore-based think tank. “Having this kind of information available publicly allows anyone to gain enough knowledge about you to impersonate you, because there are certain details like your date of birth, for instance, that are often used today by places like banks to make sure you are who you say you are.”
More importantly, the Aadhaar Act itself allows for three types of authentication to verify a person’s identity: matching an Aadhaar number with a linked fingerprint or iris, with a one-time code sent to a linked mobile number, or with a linked piece of demographic information like a residential address.
“The third type of authentication assumes that a person’s Aadhaar number is private,” said Prakash. “Having an Aadhaar number available on the public internet makes this kind of authentication unviable.”
In addition to this week’s breach, Aadhaar numbers have been made public at various times in the past. In November 2017, for instance, more than 200 government websites accidentally exposed thousands of people’s Aadhaar numbers. In May, 2017, researchers estimated that leaky government websites have exposed the data of 130 million people. And in March 2017, a government agency accidentally included the Aadhaar details of M. S. Dhoni, the captain of the Indian cricket team, in a tweet that was pulled down only when Dhoni’s wife tweeted angrily at India’s information and technology minister.
Nilekani’s critics say that he should have exercised more caution before tweeting a picture of his Aadhaar card. “He was no doubt aware that this was sensitive information that he was putting out, and it was bad precedent for him to be doing this as the most visible evangelist for Aadhaar,” said Kiran Jonnalagadda, a member of the volunteer-led Internet Freedom Foundation, which works on privacy, freedom of expression, and net neutrality issues in India.
Nikhil Pahwa, another member of the Foundation and a staunch Aadhaar critic, said that Nilekani’s “mistake shows that sometimes, even apparently tech savvy people make mistakes.” Pahwa thinks that the Aadhaar program needs a way to revoke or change an Aadhaar number — something that’s currently impossible. “While Mr. Nilekani may not personally face issues because of this foolishness,” he said, “spare a thought for common people whose Aadhaar details have been leaked.”
Quelle: <a href="The Guy Who Helped Create India’s Controversial National ID Program Leaked His Own Data, And It’s Still Online“>BuzzFeed









